Having several layers of security is necessary for protecting your computer. One of these layers should be Microsoft’s Enhanced Mitigation Experience Toolkit (EMET). It’s a more advanced tool that puts a kind of protective layer around your programs. It may take some configuration to work properly, but it’s extremely powerful and easy to use. Considering the benefits it provides and its ease of use, there is no good reason not to have it running alongside your antivirus.
Note: EMET 5.5 is the now latest version, which is not covered in this article. Find the new version download here.
Expand Table of Contents
How Does EMET Work?
When a program runs, it takes up space in your computer’s RAM (“short-term” memory). Often, if the program is not properly coded or is outdated, it will leave “holes” in the memory and cyber criminals can take advantage of those weaknesses to insert their own malicious code. EMET tries to plug those holes in the memory.
The beauty of EMET is that it’s completely independent of the applications it protects. It will work on any program, regardless of what that program’s capabilities are. That’s because EMET doesn’t fix holes by fixing the programs, but instead it goes deeper and patches the holes in the space between the program and the hardware. It works outside the program, adding a sort of protective layer in the memory.
This is extremely beneficial for several reasons. First, we don’t have to know about the existence of a software vulnerability for EMET to protect it. It can stop attacks against weaknesses that no one but the bad guy even knows about (these are called zero day vulnerabilities). Second, old programs that no longer get updated can still benefit from these newer technologies without having to modify its code.
Once EMET is up and running, you’ll probably forget it’s even there. It won’t take long to install and configuration is a snap. It even has advanced deployment options for configuring with group policy on a domain if you’re in an enterprise setting. Not to mention that it’s free.
How To Install EMET
1. Download and run the EMET installer
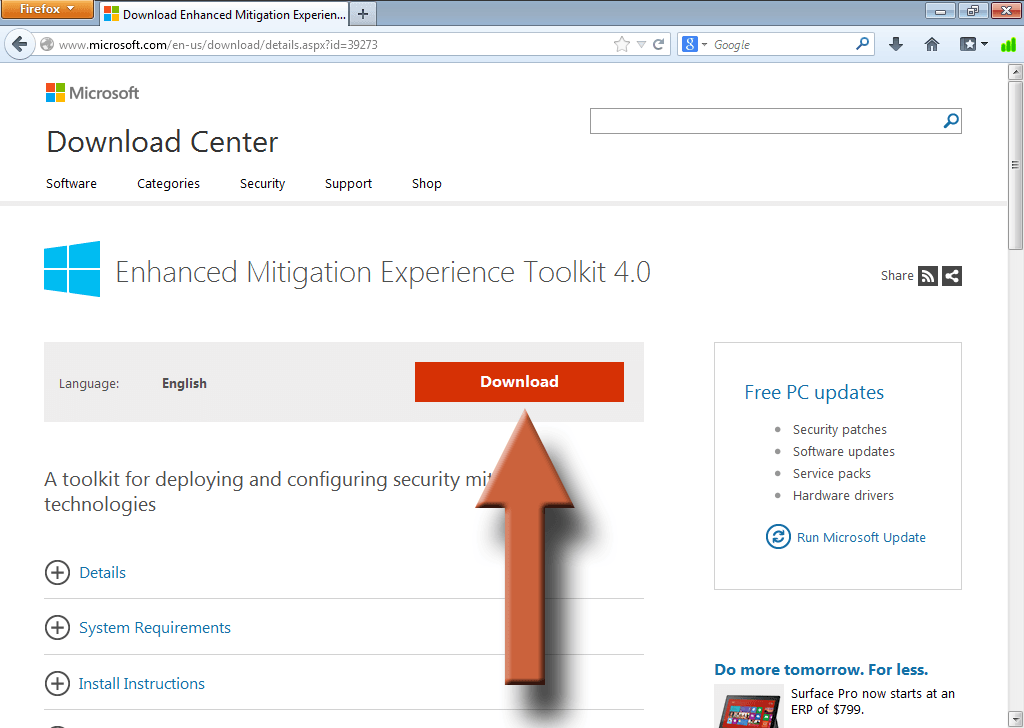
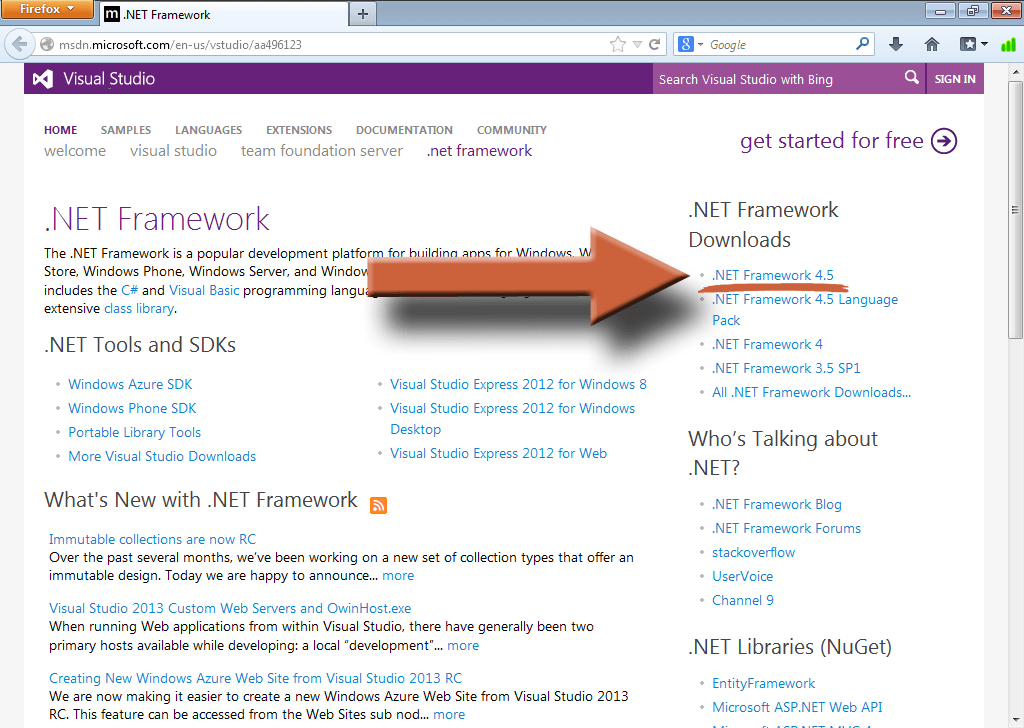
Visit the EMET download page and click on Download.
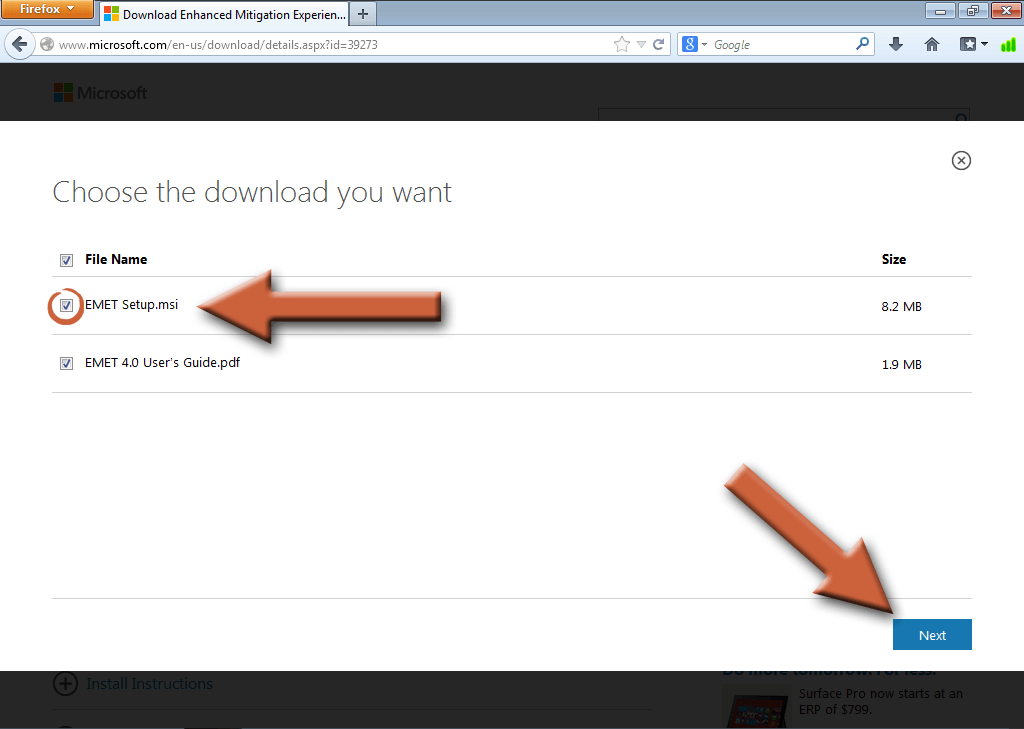
Check the box next to EMET Setup.msi and the User’s Guide if you want it. Then click Next.
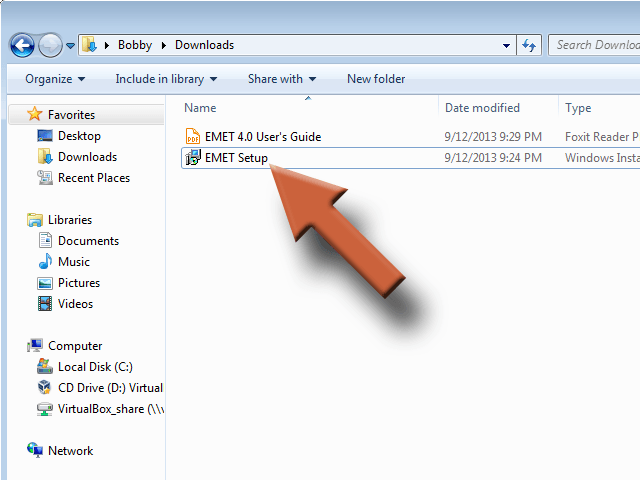
Run the file you just downloaded, EMET Setup, if it didn’t start automatically.
2. Install the .NET 4 Framework
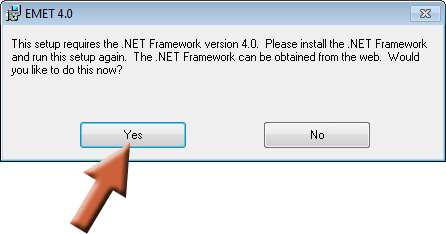
The installer will automatically check to see if you have the .NET 4 Framework on your computer since it’s required to run EMET. If you don’t, it will ask you if you’d like to install it. Click Yes. If you don’t see this window, then you should have .NET 4 already installed and don’t have to worry about it, so skip to step 3.
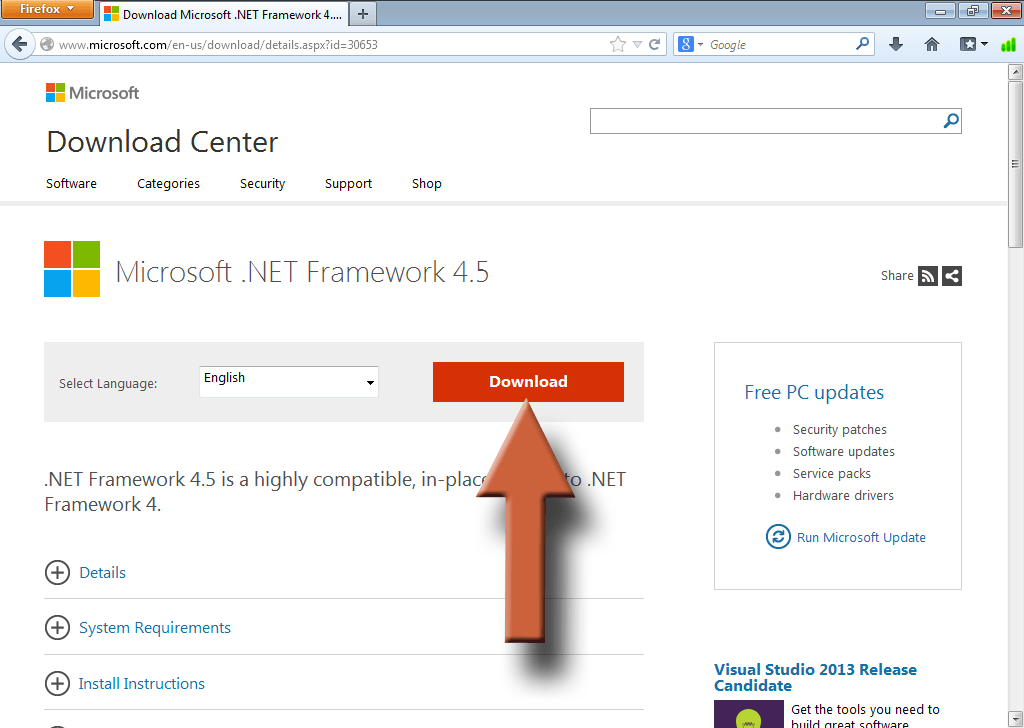
Click the .NET Framework 4.5 link on the right side of the page that just opened.
Click Download, then run the file when it’s finished, if it doesn’t start automatically. It should be called something like dotNetFx45_Full_setup. Then follow the instructions until .NET is installed.
3. Finish installing EMET
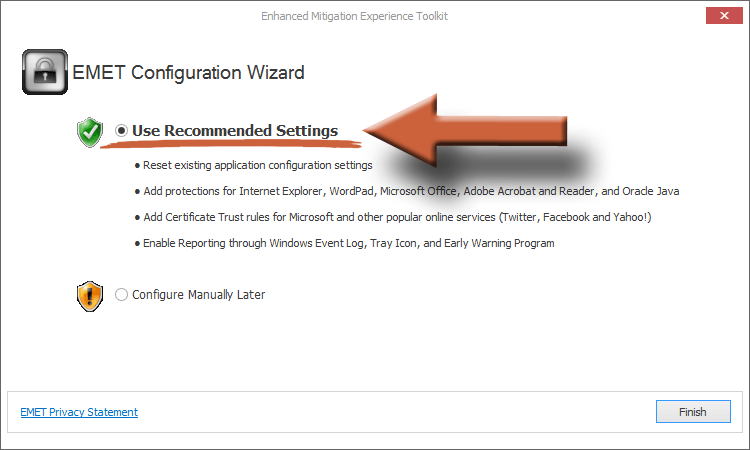
If you had to install .NET 4, then you’ll have to run the EMET installer again. Follow the onscreen instructions to install EMET until you see this screen. Make sure Use Recommended Settings is selected for the simplest configuration. Then click Finish.
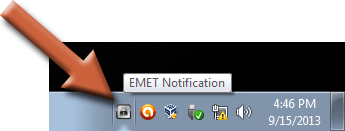
4. Make sure EMET is running
Check in your system tray in the bottom right corner of your screen. You should see an icon like the one highlighted here.
How To Use EMET
Once EMET is up and running with the recommended settings, it’s already protecting some the most vulnerable programs out there. Really, you could just stop here and already be ahead. But I would recommend soldiering on. There’s still more you can do. Don’t worry, you can’t actually break your computer. The settings are all reversible. And if worst comes to worst you can just uninstall EMET, no harm done.
1. Open the EMET window
Right click on the icon in your system tray and select Open EMET.
If you can’t find it in the system tray, go to the Start menu Programs list and find Enhanced Mitigation Experience Toolkit. The icon you will need is called EMET GUI.
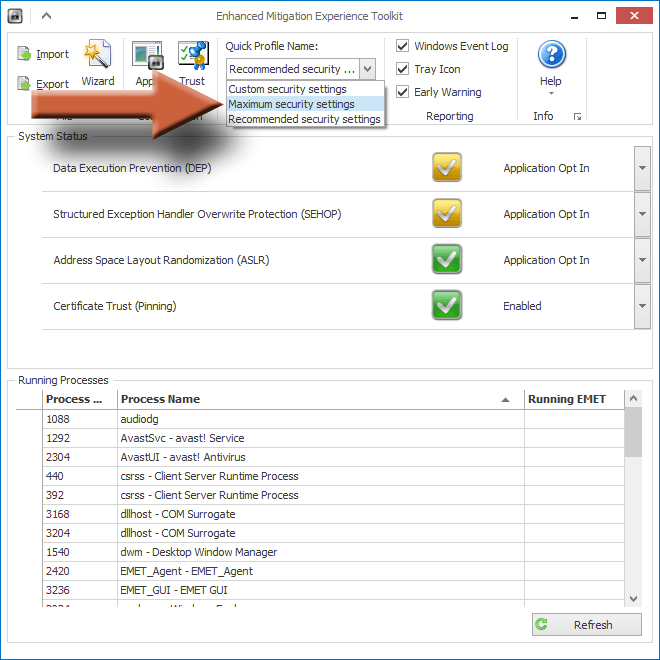
2. Change the security profile to maximum
Click the drop down menu and select Maximum security settings, then close the EMET window and restart your computer. At this point, you can just try using your computer normally for a while to test these settings. But you’re probably safe for now since we haven’t made any serious changes.
>3. Open the programs window
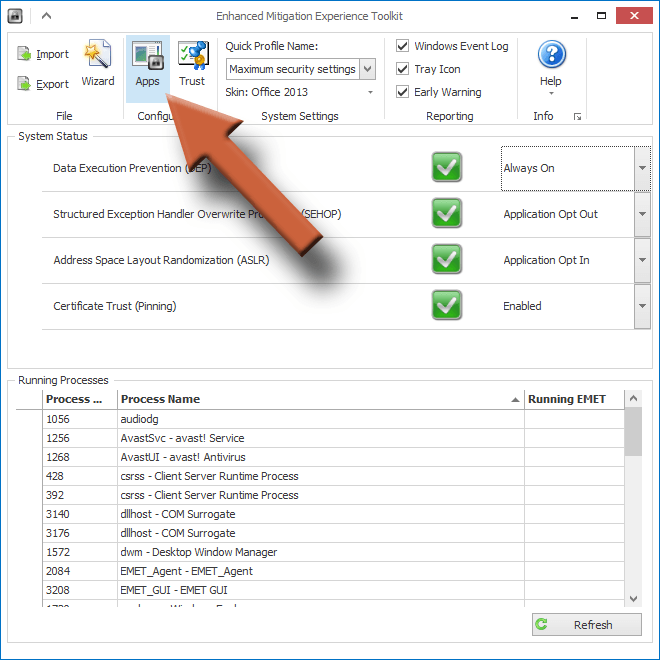
Open EMET again and click the Apps button at the top.
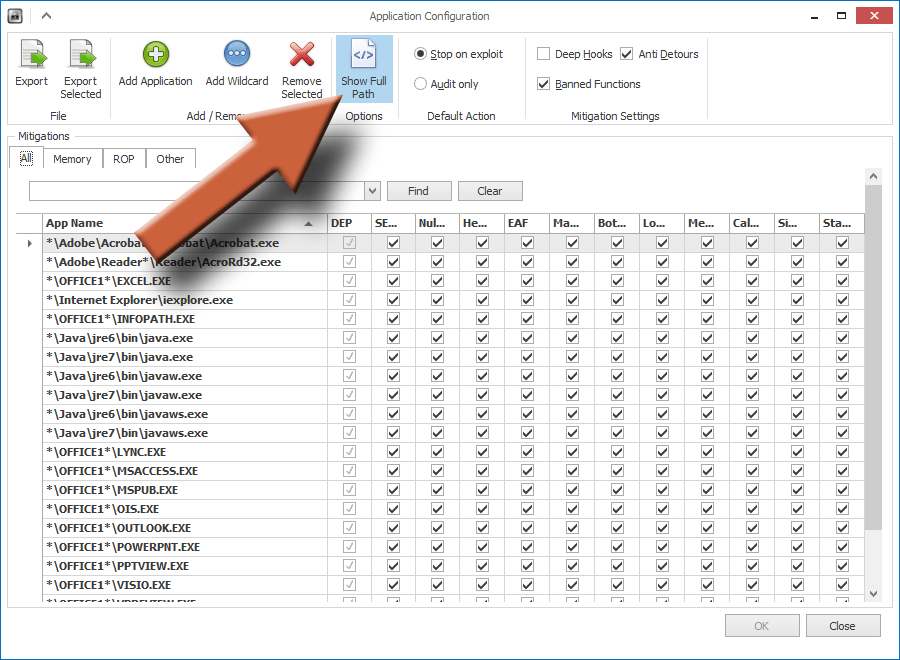
This window shows you the list of programs that EMET is currently protecting. What it’s showing you is a list of the programs’ executable file names. These can be cryptic, so you probably won’t recognize some of them. If you click Show Full Path, it will show you what folders the files are in, giving you a better idea of what the program might be.
4. Add one program to EMET that you commonly use
If you used the recommended settings during install, then you already have protection for Java, Adobe Reader and Acrobat, Office, Internet Explorer and WordPad. But we shouldn’t stop there.
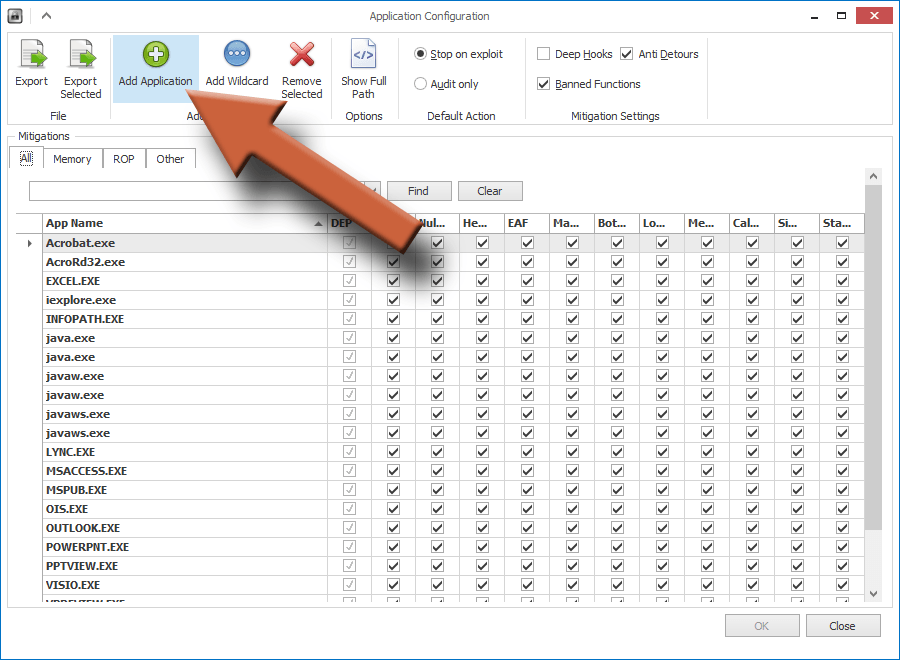
To add another program, click Add Application at the top. In the window that opens, you’ll have to find the executable file for the program you want to add. If you don’t know what that is, use my tutorial on finding a program’s executable file to track it down.
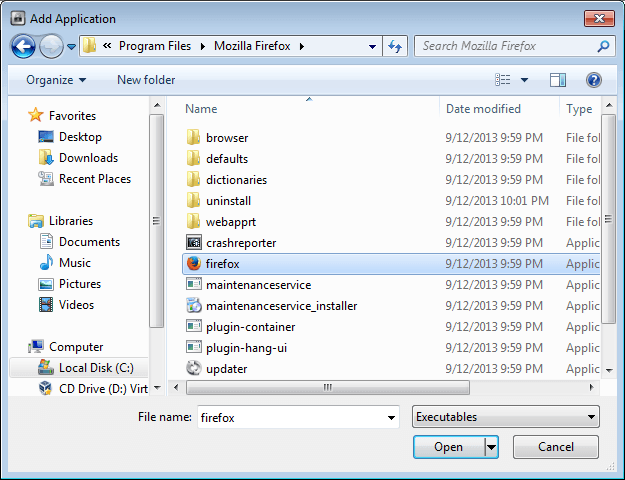
Highlight the executable file and click Open. In this example I’m adding Mozilla Firefox.
Here, you can see that it’s been added to the list of programs. Click OK.
Pay attention to the alert at the bottom of the main EMET window. If the program you added is currently running, you will have to restart it before the protection will work. You may even have to restart the computer.
5. Test the program you added
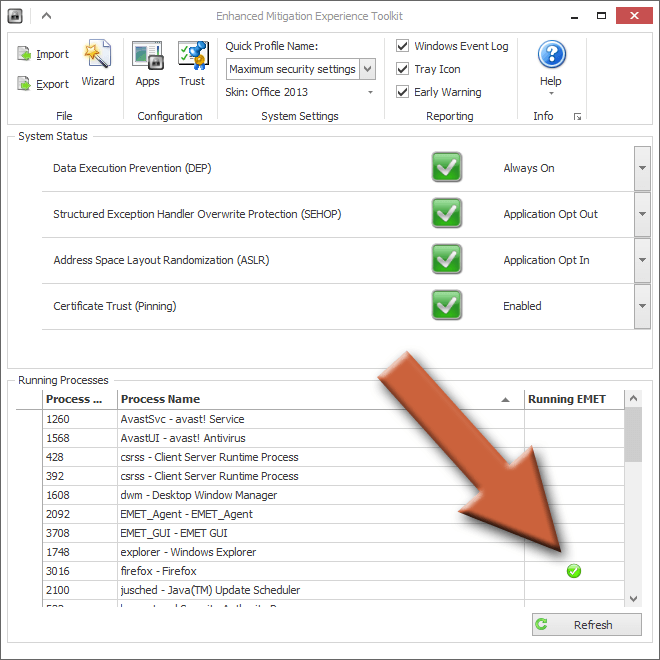
In my case, I’ll open Firefox and make sure it doesn’t have any problems running. If you go back to the main EMET window, you can see in the list of processes that Firefox is being protected, indicated by the green check mark. The check mark will disappear when I close Firefox because EMET can’t protect what’s not running.
This list on the main window only shows the currently running processes on your computer, even if they’re not being protected by EMET. The program is only being protected if it has that green check mark. For a full list of what’s being protected, go back to the Apps window.
6. Keep adding programs to EMET, one at a time
Repeat steps 4 and 5 as many times as you need to for all the programs you commonly use. But don’t make a bunch of changes at once. Because if you run into compatibility problems, it may cause some stability issues with your programs. I would recommend making one change at a time, then testing it for a while before you add another.
7. Troubleshoot problem applications
It could be that you’ll find some programs that don’t jibe with EMET. As of this writing, this forum post at TechNet has a list of known program compatibility issues. Or you can do your own troubleshooting by opening the Apps window and finding which mitigation is causing the issue by unchecking the check boxes to the right of the program one at a time, then testing testing testing.
You can also use the wizard to reset all the programs to default. This will remove any programs you manually added and revert it back to how it was when you first installed it. It does not reset the profile you selected but you can do that manually.
8. Backup your EMET configuration
Once you get EMET set the way you want it, be sure to export your settings and save it somewhere. It’s good to have a backup so you don’t have to go through all the configuration again if for some reason you have to start over, like needing to completely reinstall EMET.
Click Export in the upper left corner.
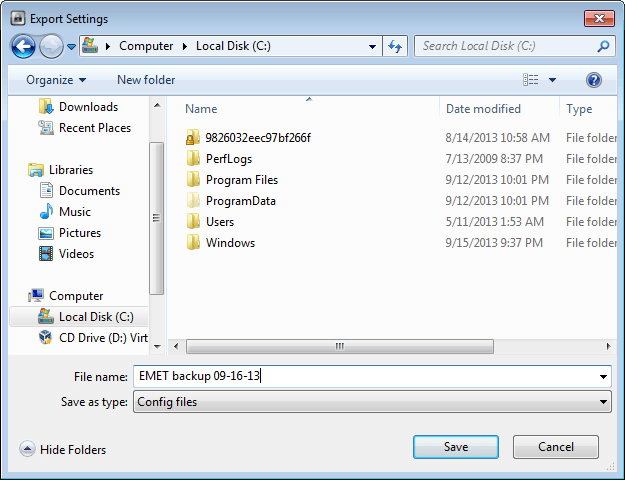
Save the config file somewhere on your computer and make sure to name it something descriptive so you remember what it is. Then back it up off your computer wherever you back up your other files.
How Do I Know if EMET is Working?
EMET will not tell you if it has protected you from something. By default, if it detects a compromised process, it will just shut down the program without any warning. However, if you have the Early Warning box checked in the main window, it will alert you that it’s sending information to Microsoft due to possible malicious activity.
If your protected program suddenly closed on you, it could be that it was attacked by malware. Or, it could also mean that it has compatibility problems with EMET.
If it happens every time you open a certain program, then chances are it’s just a compatibility issue and you’ll have to deactivate whatever mitigation is causing the problem. But if it happens just when you open a specific document, such as a PDF file for instance, but does not happen with other PDFs, then it’s most likely an infected file.
If your protected programs aren’t suddenly closing on you, then EMET isn’t detecting anything malicious. Trust the green check marks you see in the EMET window. If you have a program open and the check mark is there, then it’s being protected.
The EMET Certificate Trust
EMET includes another useful feature called Certificate Trust. This is only for browsing the web, and only works if you use the Internet Explorer browser. It will not work with Firefox, Chrome, Safari, Opera, or any other third-party browser.
Configuring and using the Certificate Trust is beyond the scope of this article as it takes some more advanced configuration. If you’re confident in working with SSL certificates and root certificate authorities, then feel free to dabble. You can’t permanently break anything.
What the Certificate Trust does is help to verify that someone hasn’t hijacked your connection to a secure website. It does this by checking that the SSL certificate matches the one from their trusted root certificate authority. If the certificate from the website is modified in any way, it could mean that there’s currently a “man-in-the-middle” attack being performed against your secure connection.
The Certificate Trust works on an individual website basis so you need to manually add every site you want protected. And it only works on secure websites (the ones that start with “https” instead of “http”). You can even modify the rules to allow certain variances in the certificate, giving it more relaxed rules to work with.
General EMET Configuration
The Main Window
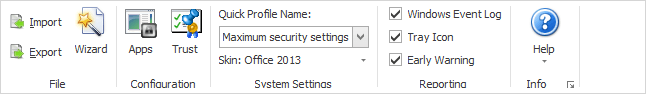
At the top of the EMET window you’ll see this “ribbon” bar, which contains several configuration options.
- Import/Export – This is where you save (export) and load (import) your EMET configuration.
- Wizard – This restarts the wizard that ran when you first installed EMET. You can use it to reset all the programs to default settings.
- Apps – Opens the application window for adding programs to EMET for protection.
- Trust – Opens the Certificate Trust window which allows you to add the secure websites you want to monitor for man-in-the-middle attacks.
- Quick Profile Name – Changes the pre-configured settings for each mitigation type, detailed in the “System Status” section right below the ribbon section. I recommend leaving it at “Maximum security settings” for the best results.
- Skin – All this does is change the appearance of the EMET window, it has no functional purpose.
- Windows Event Log – This turns on/off logging in the windows Application log. You can then use the log for advanced troubleshooting.
- Tray Icon – Toggle whether the icon shows up in the system tray (bottom right corner of the screen).
- Early Warning – If there’s a possible attack detected, this will compile all the information and send it to Microsoft for analysis.
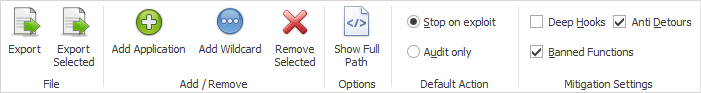
The Application Window
- Export – Allows you to save (export) the program configuration settings to a file.
- Export Selected – Allows you to save (export) only the configurations for the programs you have highlighted.
- Add Application – Used to add a program to EMET for protection.
- Add Wildcard – If you don’t want to or can’t specify an exact path to a program’s executable file, you can use wildcards (*) in the path.
- Remove Selected – Removes the selected program from EMET so it will no longer be protected. Useful if EMET is causing stability issues with a program.
- Show Full Path – Shows the whole path to the program’s executable file, instead of just the file name.
- Stop on exploit/Audit only – Tells the program to automatically terminate a compromised program or to leave it running and just audit the program instead.
- Deep Hooks – An advanced mitigation. When activated, tells EMET to protect not only the top-level APIs, but every lower level API that the top API uses. By default this is deactivated. I would recommend leaving it that way.
- Anti Detours – An advanced mitigation. Prevents some exploits from evading the mitigation techniques that EMET uses. By default, it is active. It should stay active.
- Banned Functions – An advanced mitigation. Blocks a pre-generated list of APIs from running. By default it is active and should stay that way.
EMET Tips
- If for some reason EMET is causing stability issues and you can’t figure out why, you can always uninstall it completely and start over as a last resort
- If the manual configuration of programs seems too advanced for you, you can always just leave EMET at the recommended settings and benefit to a degree from the default protection settings