Encryption is simply scrambling your information to keep it secret from eavesdroppers. Like using a Cap’n Crunch decoder ring (yes, I just dated myself).
The science of cryptography, as it’s known, is a timeless practice, going back several thousands of years to ancient Greeks, Egyptians, and Chinese. But we’re talking about computers, so why would we need a history lesson? Because computer ciphers (algorithms for encryption) are only a natural progression of the same science with modern technology.

Spartan Cryptography, by Hrana Janto
Back then, encryption ciphers were of trivial complexity, performed with pen and paper or with other similarly simple means. For example, the Cap’n Crunch decoder ring uses one of these simple methods called a “substitution cipher”. This is just replacing each letter of the alphabet with another. For instance, if you offset each letter by one, then A=B, B=C, and so on. So “attack at first light” becomes “buubdl bu gjstu mjhiu”. Extremely easy to crack, but a cipher nonetheless.
Now, with the advent of computers, we’ve developed digital ciphers with staggering complexity. Some everyday encryption methods we use for the internet would take literally hundreds of billions of years (or quadrillions, in some cases) for a modern computer to crack. That should give you some measure of peace, no?
How Encryption Works
When you encrypt a file on your computer, such as a PDF or DOC, it is turned into something that looks like random gibberish, called cipher text. This is done by running it through a complex mathematical function until it is no longer recognizable as the original data. To the onlooker, it might as well be completely random gobbledygook.
Then, to make it readable again, it’s decrypted by processing it backwards through the same function to become plain text again.
Encryption Algorithms
There are dozens of digital encryption algorithms being used out there. If you’ve ever dabbled in wireless connections or used an encryption program, then you may have heard of some of them: AES, RC4, Twofish, Blowfish, and DES to name a few. Each one has its strengths and appropriate application.
Why so many algorithms? We’re constantly having to develop new methods because they get weaker over time. Partly because vulnerabilities are found that can be exploited, but also because computing power is constantly increasing, making aging ciphers easier and easier to crack.
That’s why it’s always good to use an encryption method that’s overkill, such as using AES-256 or 512, rather than AES-128. The latter is plenty secure, but for how long? It’s always worth the effort to be future-safe.
Encryption Keys
So if we were all to use the same algorithm wouldn’t everyone’s cipher text (gibberish) look the same? Yes, unless you introduce a variable that’s unique to you: the encryption key (password).
The key is what makes your gibberish different from the next guy’s. It gets inserted into the math function and unique cipher text is generated as a result. The same key will generate the same cipher text every time you process the same data. That’s why it’s so important to try and use a key that no one else uses.
The Importance of strong encryption keys can’t be stressed enough. If a cyber bad guy gets your encrypted data, it’s possible to reverse engineer the key from it, given enough time and computing power. The stronger the key, the longer it would take to crack.
Of course, you don’t always see the encryption key. For instance, when you visit secure websites, the key is generated for you behind the scenes. In that case, you’re just trusting that the keys are strong enough to be secure.
Just to be clear, not all passwords are encryption keys. The terminology gets confused in everyday use. Technically, passwords are simply used to give you access to something. But only encryption keys are used to encrypt data, even though we tend to call them passwords sometimes. For instance, your wireless password is actually an encryption key.
What Is Encryption Used For?
We use digital encryption for a lot of things. Below are some common practices that will have an impact on every user in some way.
- Wireless connections
- Hard drives and flash drives
- Internet encryption
- Email encryption
- Hashing
Because wireless data is sent through the air, it’s extremely easy to capture. You absolutely need encryption enabled on all your wireless connections. This includes WiFi, Bluetooth and RF devices, ad hoc, etc.
It’s becoming more common for people to encrypt their hard drives, especially on their laptops and other portable devices because they can get lost or stolen so easily. The same goes for thumb drives. Remember that password-protected does not mean encrypted.
With so many threats on the internet, creating secure connections to websites is critical when you transfer sensitive information. When you see “https” (instead of “http”) in the address, it means you have an encrypted connection to the webpage.
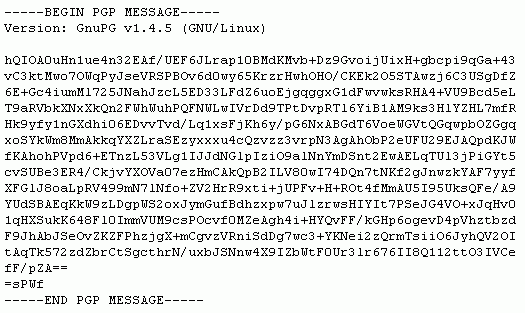
Email is by default unencrypted. Very few people actually go the extra mile to ensure their email communication is encrypted because it’s kind of a chore to do and it requires that both the sender and recipient have the ability. PGP encryption is a popular method for email.
Not technically encryption as it’s only a one-way process. The hashed data cannot be decrypted once it’s encrypted. Hashing is typically only used to store data for future reference, such as in password databases or to verify the integrity of files. Some popular hash algorithms are SHA and MD5.
Related articles